(We are again pleased to welcome a guest post this week. There has recently been a sharp increase in phishing attacks so here is good advice from our associate Olubowale Sangosanya of isecurdata on how to keep yourself safe.)
It is believed that a whopping 91% of cyber-attacks start with a phishing email, that is, most other forms of cyber-attacks are deployed via a malicious phishing email, the high success rate is due to its unique feature of exploiting human flaws such as greed and fear.

What is Phishing
Phishing is a type of social engineering attack often used to steal user data or information, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes or deceive an individual into opening an email, instant message, or text message. The recipient is then tricked into clicking a malicious link, which would most times lead to an installation of malicious code or malware.
Phishing Attacks
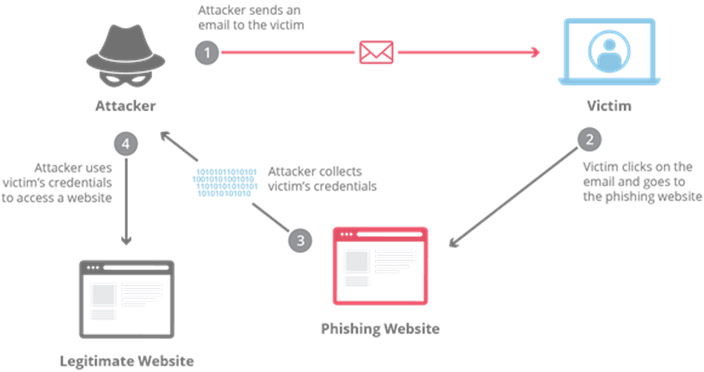
A classic example was the RSA attack back in 2011. The email, which contained an attachment, called “2011 Recruitment plan.xls was not itself sophisticated however, it was highly successful because it was targeted to a number of people within the organisation, which was enough to trick one of the employees to open the attached excel file.
The diagram below shows graphical representation of how this is carried out.
History of Phishing
Phishing is an attack method that has been around since the mid-1990. It started when a group of teenagers decided to use AOL’s chat room feature to impersonate AOL administrators. They wanted to ensure they would always have free AOL access, so they needed credit card numbers. AOL had a “new member chat room” where someone could go for assistance with their access. The hackers, DaChronic and his friends, would create what appeared to be valid AOL administrator’s screen names like “Billing Accounting” and inform the user there was a problem with their account. They simply then needed to provide their card number again to get the problem fixed. The hackers then had a card number to charge their service to. They coined the term phishing at that time. It has now come to primarily be associated with email scams.
Phishing statistics
1. 80% of reported security incidents are due to Phishing attacks.
2. A new Phishing site launches every 20 seconds
3. 1 in 25 branded emails are described as phishing emails.
4. 75% of organisations around the world experienced phishing attack in 2020.
5. 1 in 3 of data breaches recorded in 2018 involves phishing
6. 65% of organisations faced Business Email Comprise (BEC) attacks.
7. 48% of malicious email attachments are office files.
8. 84% of SMBs are targeted by Phishing attacks
9. 94% of malware is delivered by email.
10. In 2018, the detection of URL phishing increased by over 250%
11. KnowBe4: 37.9% of Untrained Users Fail Phishing Tests
12. Verizon DBIR 2020: Phishing is the biggest cyber threat for SMBs, accounts for 30% of SMB breaches
Types of phishing and examples
Email – Most phishing attacks are sent via email. Attackers typically register fake domain names that mimic real organizations and send thousands of common requests to victims. For fake domains, attackers may add or replace characters (e.g. my-bank.com instead of mybank.com) use subdomains (e.g. mybank.host.com) or use the trusted organization’s name as the email username (e.g. mybank@host.com).
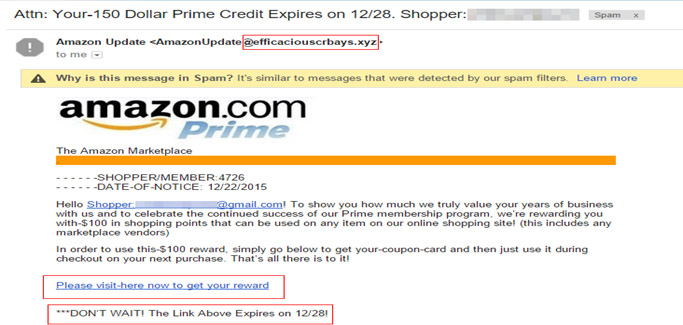
A typical and popular example is the Amazon phishing scam.
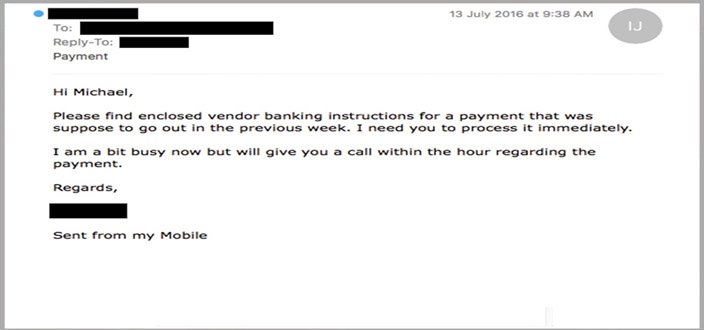
Spear – This sort of attack is usually targeted towards specific people. A typical example are executives and business decision makers. The attacker would typically have some or all the information of the intended victim.
– Name
– Place of employment
– Job title
– Email address
– Specific information about their job role
– Trusted colleagues, family members, or other contacts, and samples of their writing.
This information helps increase the effectiveness of phishing emails and manipulate victims into performing tasks and activities, such as transferring money.
Whaling – Whaling attacks target senior management and other highly privileged roles. The goal of whaling is the same as other types of phishing attacks, but the technique is often very subtle. Senior employees commonly have a lot of information in the public domain and attackers can use this information to craft highly effective attacks.
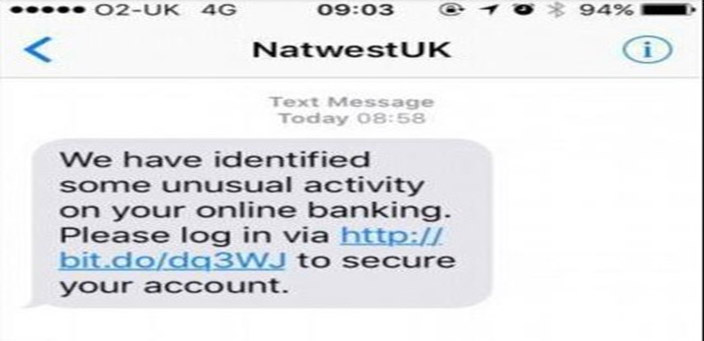
Smishing and Vishing – This is a phishing attack that uses a phone instead of written communication. Smishing involves sending fraudulent SMS messages, while vishing involves phone conversations.
Angler – These attacks use fake social media accounts belonging to well-known organizations. The attacker uses an account handle that mimics a legitimate organization (e.g. “@pizzahutcustomercare”) and uses the same profile picture as the real company account.
How to identify phishing email
Identifying phishing emails use to be straightforward as most emails usually come with wrong spellings and bad grammar but as hackers continue to refine their works and attacks become more sophisticated, phishing emails can only be identified by its features.
Below are key features of a phishing email.
1. Subject Line – Phishing emails typically aim to employ scare tactics by using intense words to create some sort or urgency, this is done to induce the recipient into responding quickly, without recognizing the signs of a scam.
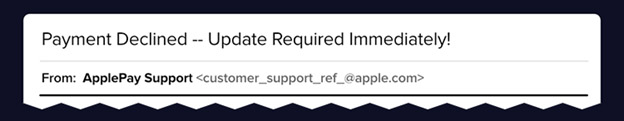
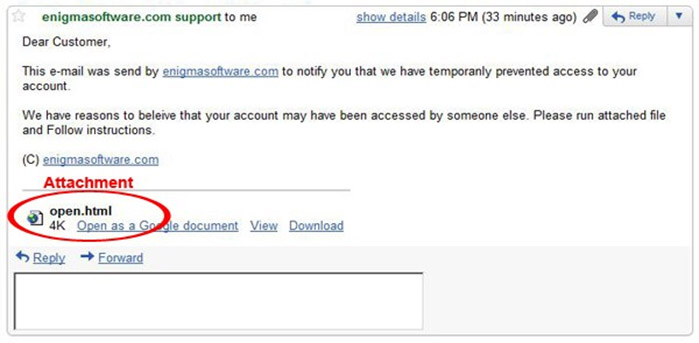
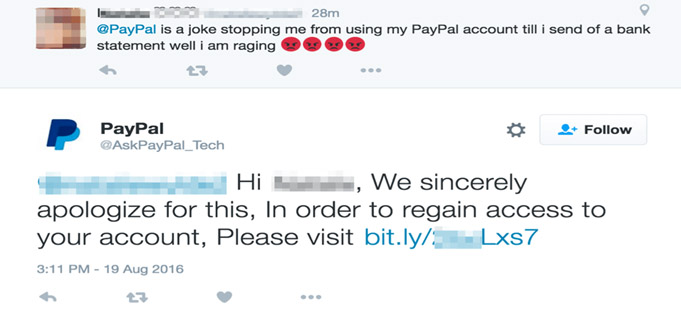
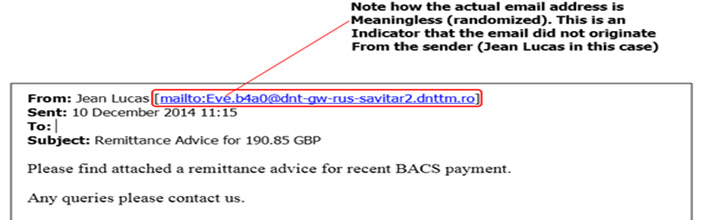
2. From field – To work, phishing campaigns must trick the email recipient into believing that the message is from a reputable company. As such, the email will appear to come from a legitimate entity within a recognized company, such as customer support. Upon closer look, however, you can see that both the name of the sender and the sender’s email address is a spoof on a known brand, not a real vendor.
3. To Field – Phishing emails are usually not personalized, they are addressed as user/customer which is a red flag, and most organizations refer to customers by name when addressing critical issues.
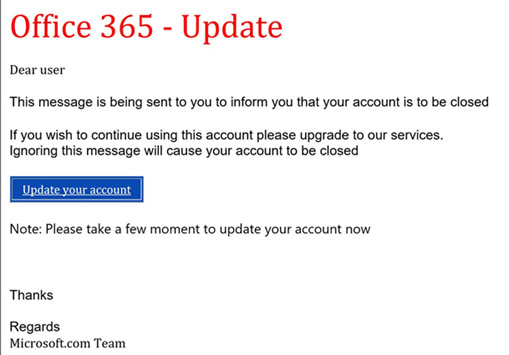
4. Email Body – Similar to the subject line, the body of the email also employs scare tactics, urging you to either click on a link, respond to an email, download an attachment or call a telephone number.

5. Malicious Link – A suspicious link is one of the main giveaways of a phishing email. These links are often shortened (through bit.ly or a similar service) or, as above, are formatted to look like a legitimate link that corresponds with the company and message of the fake email. However, rolling over the link shows a malicious address that doesn’t take you to the stated web address.

6. Attachment – Including malicious attachments that contain viruses and malware is a common phishing tactic. Malware can damage files on your computer, steal your passwords or spy on you without your knowledge. Don’t open any email attachments you weren’t expecting.
How to prevent Phishing
There are several things one can do to prevent a successful phishing attack. As its name implies, this is when hackers go about fishing for data with enticing emails, texts and or websites with the intended goal of gaining valuable information.
There are some very specific things that individuals can do in order not to fall a victim of this attack.
1 Always double check before clicking on any link in an email.
2 Be cautious about opening email if you don’t recognize the sender.
3 Look at the subject line and check for typos or incorrect information.
4 Be wary of emails asking for your Credit Card or other confidential information
5 Never respond to requests for personal information via e-mail.
6 Check to make sure the Web site is using encryption
7 Only visit Web sites by typing the URL into your address bar or using your favorites
8 Use of 2FA authentication on accounts where possible
9 Be suspicious of pop-ups and pop-unders.
10 Be suspicious of email attachments from known and unknown sources.
This boil down to a simple, yet often difficult things to do, be a bit paranoid about anything you can click on or anyone you could talk to. If it sounds too good or too bad to be true, it probably is.
For organisations, in addition to the above recommendations, the following are also recommended as it serves as good practice.
• Regular cybersecurity awareness training.
• Authenticate email senders using Domain-based Message Authentication, Reporting and Conformance (DMARC).
• Filter for phishing emails based on sender, content, and analyse URLs and attachments for malicious codes.
• Filter for phishing email and malicious web traffic at the gateway.